-
Notifications
You must be signed in to change notification settings - Fork 2
New options for Patient masking #155
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Conversation
src/helpers/patientUtils.js
Outdated
| patient._multipleBirthInteger = masked; | ||
| } | ||
| } else if (field === 'photo' && 'photo' in patient) { | ||
| delete patient.phoo; |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
| delete patient.phoo; | |
| delete patient.photo; |
Superrrr small typo
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Good catch! Addressed in commit 713e4ce
|
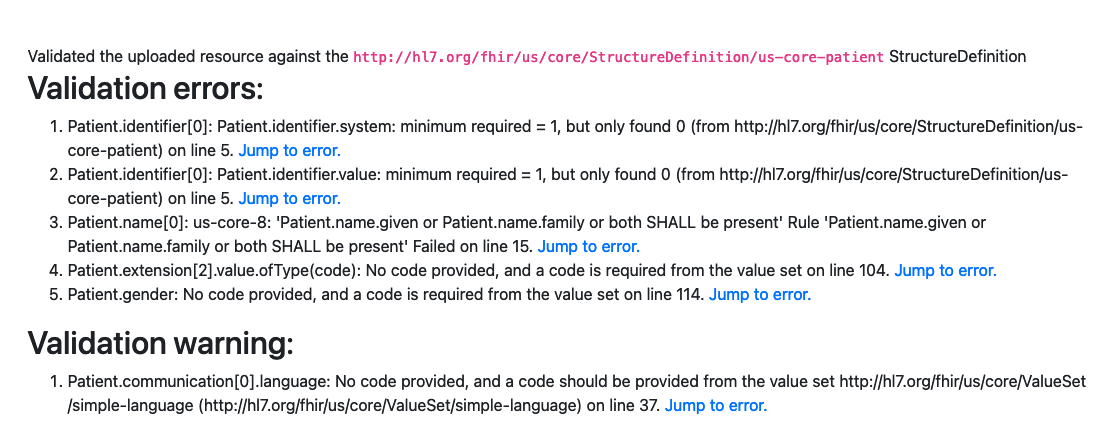
Overall this looks great to me. The one other thing I'll remark on is the resulting bundle is failing validation according to Inferno's online validator. The errors I see are screncapped below. That said, I feel confident that our modelling of data-absent-reason for primitive values is correct based on FHIR's documentation. I raise the point in case I'm 1) getting different validator results than you, 2) missing another aspect of this problem that might be interesting. tl;dr once my super small typo above is addressed, I'm good to approve; modelling data-absent extensions on primitives is hard; validating against them is harder. |
83928b0 to
713e4ce
Compare
I got the same errors and warnings when I ran the validation myself. They seem to be unavoidable for us in the sense that the elements causing them do actually require the properties being detected by the validator, but that including those required bits does amount to PII that's being masked in the first place. Some of these errors could be avoided by including some nebulously appropriate values for some of these elements (perhaps included |
To be clear, I think what we have so far is perfect and the ideal. Just bizarre that validators don't seem keen on handling the else-if case where, if that property cannot be found, then check to see if there is an appropriate data-absent-reason. Might be something to discuss with the inferno team at some point. As far as this goes, I'm good to approve |
Summary
Makes the following elements in the Patient resource maskable:
telecom,multipleBirth(bothmultipleBirthBooleanandmultipleBirthInteger),photo,contact,generalPractitioner,managingOrganization, andlink.New behavior
No changed behavior. The above elements are now supported as options within the
maskarray of the PatientExtractor config.Code changes
maskPatientDatafunction.extended-patient-bundle.json) was added to test masking, given that the newly supported fields are not supported by the CSVExtractors and will only ever occur in resources obtained via a FHIR search.Testing guidance
_s are placed before primitive elements, and that array elements have their dataAbsentReason extension contained within an array).