-
Notifications
You must be signed in to change notification settings - Fork 231
Improve extensions + submissions autocomplete #1532
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Conversation
|
Have you tested with names containing characters that would be entity encoded (I used ' ( Did you verify that the flash xss occurs without these changes? the flash rendering seems safe already: |
|
Re: flash, I recall that the success flash did not escape I will also test for double encoding later. |
|
OK - Admittedly |
|
Is this still WIP or is it ready for review? |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
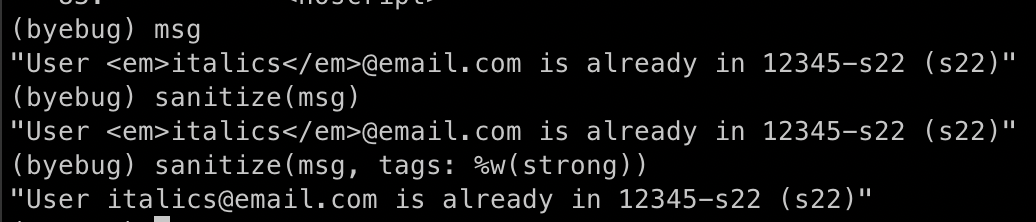
it seems pointless to call sanitize() after escape_html(). sanitize won't find anything to filter because escape_html has already encoded all the tag metacharacters.
It appears that if you don't call sanitize, you don't need escape_html either, because rails will automatically escape the inner text of the content_tag.(https://makandracards.com/makandra/2579-how-to-use-html_safe-correctly)
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Instead of this, it might make sense to have the controller use strict_encode64 instead of urlsafe_encode64 (my bad there)
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I suppose I'll have to test this at some point, but I don't see how this can avoid breaking the autocomplete in some cases. the keys in usersEncoded have to match the keys in users. They differ only in whether or not they're encoded. If the keys don't match, the user can't be autocompleted.
|
Re: Re: Re: autocomplete, I'm not sure which line of code you're specifically referring to. However, I don't see any immediate issues with the current approach. Could you clarify this? |
|
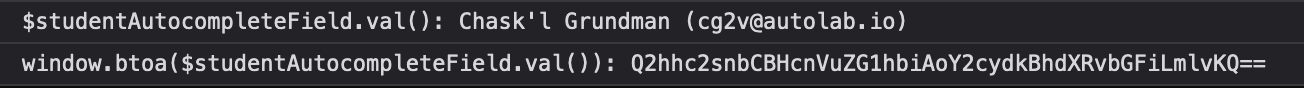
Say my name is
Then When the javascript calls btoa on Chask'l Grundman ([email protected]), it gets Q2hhc2smYXBvcztsIEdydW5kbWFuIChjZzJ2QGF1dG9sYWIuaW8p which does not match. However, the existing code is broken if there are tags in the name (materialize strips the tags - there's no xss). So perhaps the correct thing to do is to escapeHTML before encoding. Things are getting very hacky at this point and it leads me to wonder how other software deals with this problem. |
|
Also note that I am doing Essentially, it seems that the autocomplete code unescapes once when displaying text (such that An Example |
|
Alternatively, |
|
If that's what autocomplete is doing, I will withdraw my objections |
|
@victorhuangwq This PR is ready for review! |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Tested the functionality as given by the test case, works as expected.
Good that you abstracted repeated functionality!
I approved, but I had a nit. Thanks for addressing this issue.



Improve correctness of extensions + submissions autocomplete, and extract common logic.
Also fix an XSS issue in gradebook, and various visual display issues.
Description
CGI.escapeHTMLon backendescape_javascripton frontendsanitizefrom flashencode64withstrict_encode64to avoid line feedsApplicationControllercomponents/_autocomplete.html.erbto_csvfordownload_rosterMotivation and Context
Currently, there are several issues with autocomplete, including
This PR serves to improve the robustness of extensions + submissions autocomplete
How Has This Been Tested?
First created the following users:
(invalid emails can be saved by using inspect element and deleting the type from the input field)
\back\slash[email protected]<img src=a onerror=alert(document.cookie)>alert[email protected]<strong>first</strong><strong>last</strong>[email protected]qn?mark[email protected]/Space(with a leading space)Name[email protected]italicsemail<em>name</em>@italicsemail.combademail<strong>name</strong>@bademail.comscriptemail<script>alert("hello")</script>@scriptemail.comTypes of changes
Checklist:
overcommit --install && overcommit --signto use pre-commit hook for linting