-
Notifications
You must be signed in to change notification settings - Fork 2
handle unauthorized calls' return #1665
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Conversation
|
Using
also in the future when we add more providers, we won't worry about this issue again and taking in consideration the alert and global error handler in one place if we want to do so !? |
|
I Believe in having one interceptor all the components using it (Core, EE) is much better than having it two times. |
|
let's stick to EE then |
|
Yeah we want to avoid multiple ways of doing this if possible. Can we keep using the import { maybeLogout } from "@weaveworks/weave-gitops";
...[snip]...
onError: error => { maybeLogout(error); }Agree having the logic in a single spot is nice. However should the handlers be on the |
…erprise into fix-unhandeled-auth-redirect
|
In prev commit i used Right, so we're keeping the error handler to useQuery and removing |
…erprise into fix-unhandeled-auth-redirect
Yes, does this approach work in core too? E.g. when working with the login handlers themselves or do they need to escape this somehow? Maybe they already use the
My concern is that the queryCache handlers are always there, while doing it on the query-client only set defaults which we would be overriding in some places right now (e.g. weave-gitops-enterprise/ui-cra/src/hooks/templates.tsx Lines 16 to 24 in 00e3681
It would be nice to avoid a "flash of error message" before redirecting but maybe its unavoidable using this approach.. |
Yes, core uses react-client as well
it's unavoidable yes
In this case we might move the the notification to the shared |
…erprise into fix-unhandeled-auth-redirect
…veworks/weave-gitops-enterprise into fix-unhandeled-auth-redirect
|
@foot, what do you think 👆 ? |
ui-cra/src/App.tsx
Outdated
| code: number; | ||
| message: string; | ||
| } | ||
| const queryClient = new QueryClient({ |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
do we need any unit tests for this behaviour?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Tested that works and the change make logical sense to me so approving based on that.
@TheGostKasper other concerns like interceptors or oss compatibility has not been considered ... in case you think they are a required before merge, other folks might need to check
my last suggestion would be to add some level of automated testing before merging
Closes
What changed?
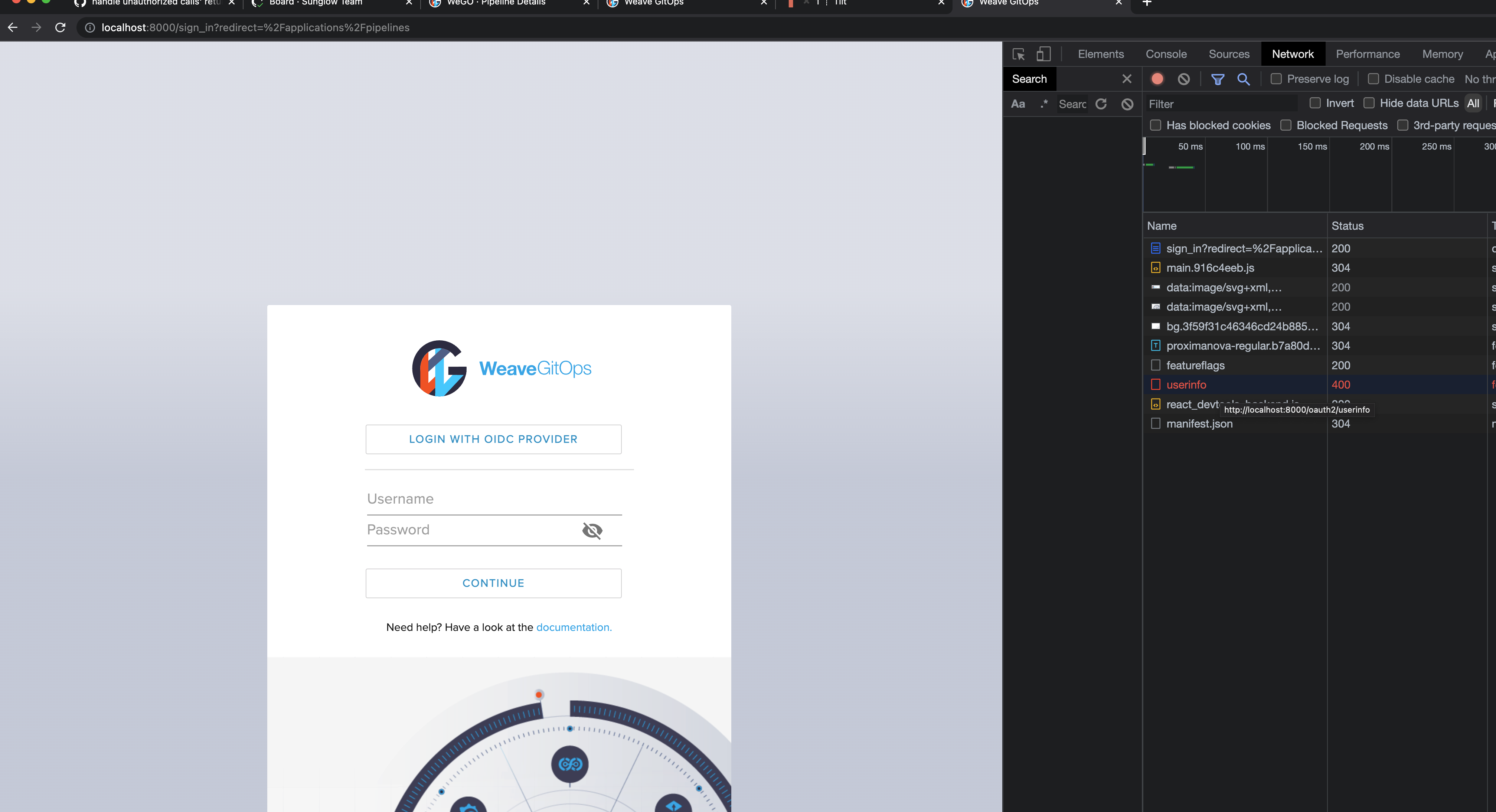
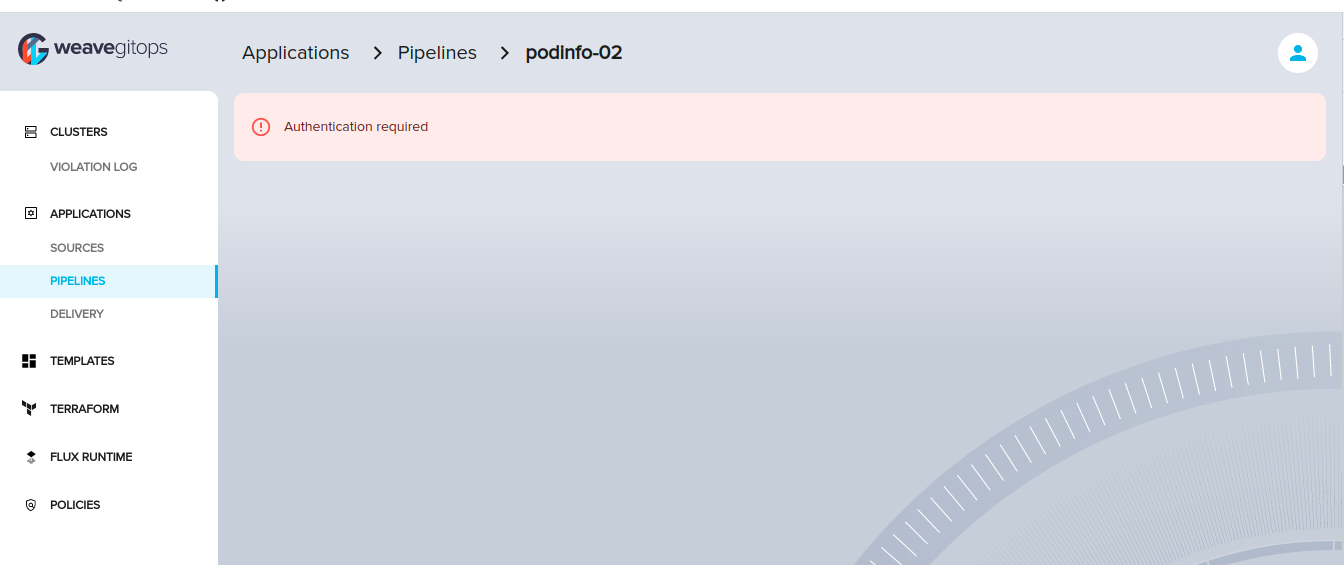
Provide a redirect to signin form when unauthorized call is emitted