Prerequisites
To get started, you need the following items:
An Azure AD subscription. If you don't have a subscription, you can get a free account. Dynatrace single sign-on (SSO) enabled subscription.
- Add Dynatrace from the gallery to Azure
- Configure Azure AD SSO
- Configure Dynatrace SSO
- Test SSO
1. Add Dynatrace from the gallery
To configure the integration of Dynatrace into Azure AD, you need to add Dynatrace from the gallery to your list of managed SaaS apps.
- Sign in to the Azure portal using either a work or school account, or a personal Microsoft account.
- On the left navigation pane, select the Azure Active Directory service.
- Navigate to Enterprise Applications, and then select All Applications.
- To add new application, select New application.
- In the Add from the gallery section, type Dynatrace in the search box.
- Select Dynatrace from results panel and then add the app. Wait a few seconds while the app is added to your tenant.
Configure and test Azure AD SSO for Dynatrace
Configure and test Azure AD SSO with Dynatrace using a test user called Vihan.D. For SSO to work, you need to establish a link relationship between an Azure AD user and the related user in Dynatrace.
To configure and test Azure AD SSO with Dynatrace, complete the following building blocks:
- Configure Azure AD SSO - to enable your users to use this feature.
- Create an Azure AD test user - to test Azure AD single sign-on with tushar.
- Assign the Azure AD test user - to enable tushar to use Azure AD single sign-on.
- Configure Dynatrace SSO - to configure the single sign-on settings on application side.
- Create Dynatrace test user - to have a counterpart of tushar in Dynatrace that is linked to the Azure AD representation of user.
- Test SSO - to verify whether the configuration works.
2. Configure Azure AD SSO
Follow these steps to enable Azure AD SSO in the Azure portal.
- In the Azure portal on the Dynatrace application integration page, find the Manage section and select single sign-on.
- On the Select a single sign-on method page, select SAML.
- On the Set up single sign-on with SAML page, click the pencil icon for Basic SAML Configuration to edit the settings.
- In the Basic SAML Configuration section, the application is pre-configured in IDP initiated mode and the necessary URLs are already pre-populated with Azure. The user needs to save the configuration by clicking the Save button.
- Click Set additional URLs and complete the following step to configure the application in SP initiated mode:
- In the Sign-on URL text box, type the URL: https://sso.dynatrace.com/
On the Set up single sign-on with SAML page, in the SAML Signing Certificate section, find Federation Metadata XML. Select Download to download the certificate and save it on your computer.
- In the SAML Signing Certificate section, select the Edit button to open the SAML Signing Certificate dialog box. Complete the following steps:
a. The Signing Option setting is pre-populated. Please review the settings as per your organization.
b. Click Save.
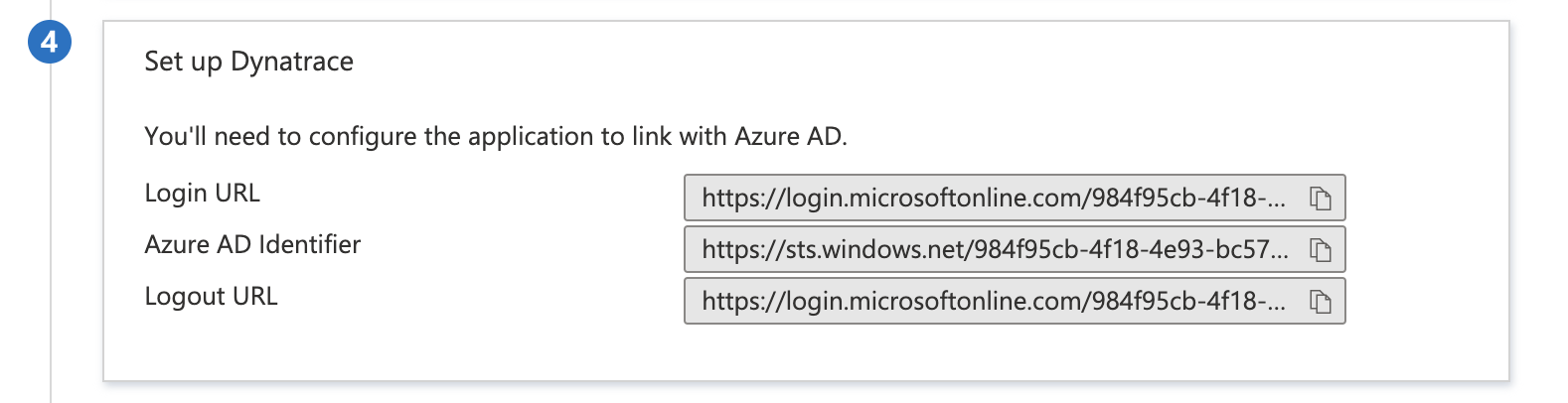
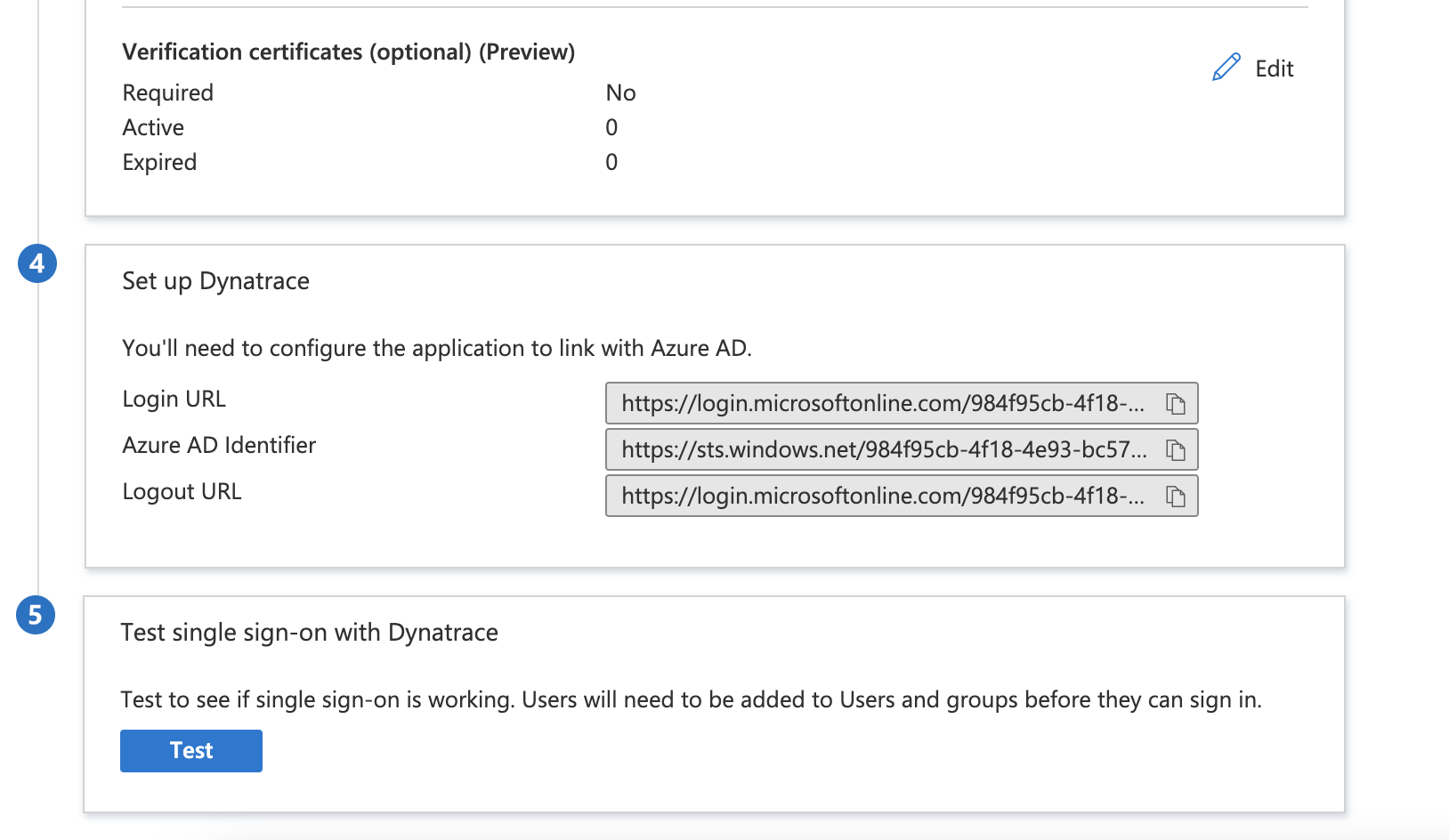
In the Set up Dynatrace section, copy the appropriate URL(s) based on your requirement.
Create an Azure AD test user
- From the left pane in the Azure portal, select Azure Active Directory, select Users, and then select All users.
- Select New user at the top of the screen.
- In the User properties, follow these steps:
- In the Name field, enter tushar.
- In the User name field, enter the [email protected]. For example, [email protected]
- Select the Show password check box, and then write down the value that's displayed in the Password box.
- Click Create.
Assign the Azure AD test user
In this section, you'll enable vihan to use Azure single sign-on by granting access to Dynatrace.
- In the Azure portal, select Enterprise Applications, and then select All applications.
- In the applications list, select Dynatrace.
- In the app's overview page, find the Manage section and select Users and groups.
- Select Add user, then select Users and groups in the Add Assignment dialog.
- In the Users and groups dialog, select vihan from the Users list, then click the Select button at the bottom of the screen.
- If you are expecting a role to be assigned to the users, you can select it from the Select a role dropdown. If no role has been set up for this app, you see "Default Access" role selected.
- In the Add Assignment dialog, click the Assign button.
3. Configure Dynatrace SSO
- Goto Account Settings (below the account details in top right corner).
- Choose Identity management from the application’s left-hand navigation to configure user access to the Dynatrace application.
- Click on Single sign-on
- Enter domain name and verify it
- Copy the value and create TXT record in your route 53 to verify it.
- After verification you will see it added in the verified domain.
-
click on the edit configuration
-
In Upload XML, provide the metadata you downloaded as Federated Metadata XML and set the following attributes:
First name attribute http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname Last name attribute http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname Security group claim attribute http://schemas.microsoft.com/ws/2008/06/identity/claims/groups
- Click on validate configuration
4. Test SSO
-
Click on Test this application in Azure portal. This will redirect to Dynatrace Sign on URL where you can initiate the login flow.
-
Go to Dynatrace Sign-on URL directly and initiate the login flow from there.
Logged in with the new user "[email protected]"
Enter the mail id of user which you created.
You will be able to login to dynatrace using username only.
References:
- https://learn.microsoft.com/en-us/azure/active-directory/saas-apps/dynatrace-tutorial
- https://www.dynatrace.com/support/help/how-to-use-dynatrace/user-management-and-sso/manage-users-and-groups-with-saml/saml-azure
- https://www.dynatrace.com/support/help/how-to-use-dynatrace/user-management-and-sso/manage-users-and-groups-with-saml/saml-azure#expand--example-search-for-dynatrace-application
- https://aws.amazon.com/blogs/apn/aws-single-sign-on-integration-guide-for-dynatrace/