-
Notifications
You must be signed in to change notification settings - Fork 549
doc: Image promotion policy #4762
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Merged
Merged
Changes from 11 commits
Commits
Show all changes
13 commits
Select commit
Hold shift + click to select a range
4cb8975
Created Doc Structure
ashokdevtron d7844e9
Promotion Policy Doc with RBAC
ashokdevtron d7e29fa
Fixes
ashokdevtron af46c14
CO Feedback Incorporated
ashokdevtron 75f0078
Snapshots Added + PM/CO Feedback Incorporated
ashokdevtron 5d38141
Figure Corrections
ashokdevtron 88ee29e
Added Promotion Approval Snap + Artifact Approver role
ashokdevtron 2d55d34
Final Fixes
ashokdevtron 74e4e92
Reworked PM Feedback
ashokdevtron 18de7a2
Added CLI steps + Fixes + PM Feedback
ashokdevtron 3fe4ec6
doc: updates CD filter def
abhibhaw efd71d6
Fixes and Corrections
ashokdevtron 0d9f1d2
Merge branch 'main' into image-promotion-policy
ashokdevtron File filter
Filter by extension
Conversations
Failed to load comments.
Loading
Jump to
Jump to file
Failed to load files.
Loading
Diff view
Diff view
There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
260 changes: 260 additions & 0 deletions
260
docs/user-guide/global-configurations/image-promotion-policy.md
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,260 @@ | ||
| # Image Promotion Policy | ||
|
|
||
| ## Introduction [](https://devtron.ai/pricing) | ||
|
|
||
| An ideal deployment workflow may consist of multiple stages (e.g., SIT, UAT, Prod environment). | ||
|
|
||
|  | ||
|
|
||
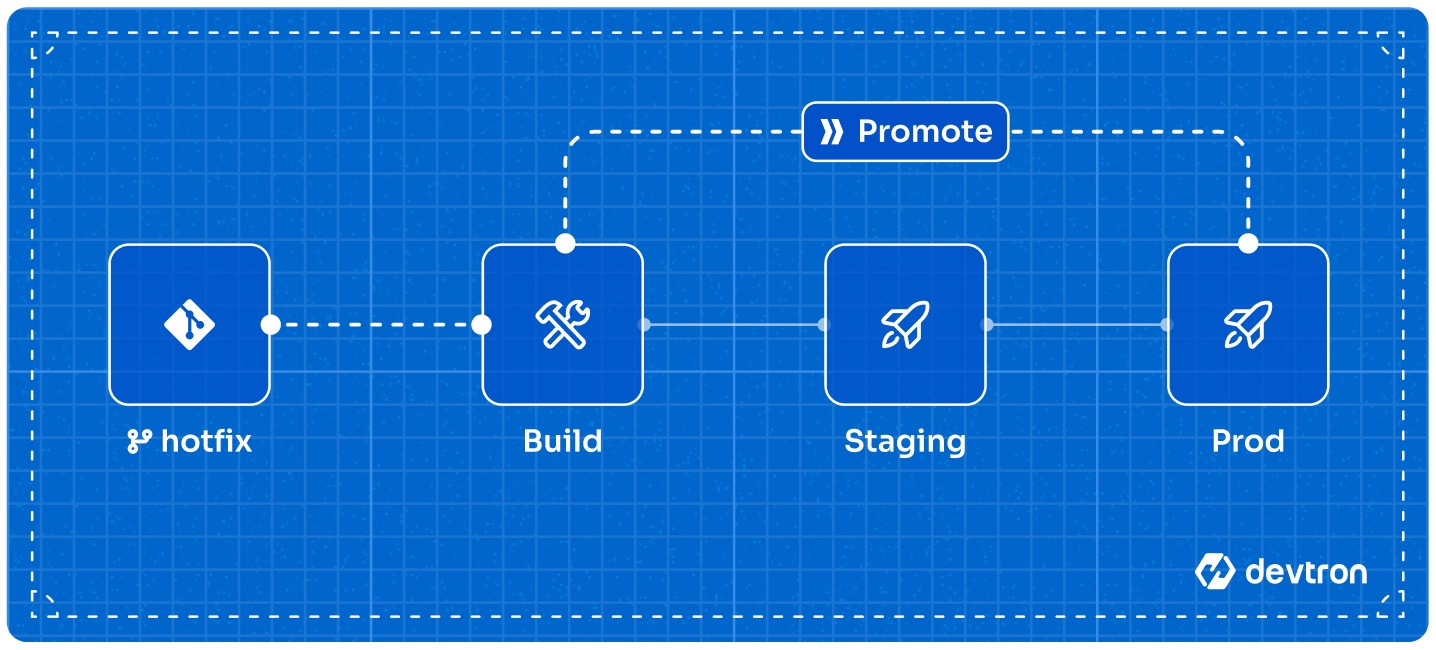
| If you have built such a [workflow](../creating-application/workflow/README.md), your CI image will sequentially traverse and deploy to each environment until it reaches the target environment. However, if there's a critical issue you wish to address urgently (through a hotfix) on production, navigating the standard workflow might feel slow and cumbersome. | ||
|
|
||
| Therefore, Devtron offers a feature called 'Image Promotion Policy' that allows you to directly promote an image to the target environment, bypassing the intermediate stages in your workflow including: | ||
|
|
||
| * [Pre-CD](../creating-application/workflow/cd-pipeline.md#pre-deployment-stage) and [Post-CD](../creating-application/workflow/cd-pipeline.md#post-deployment-stage) of the intermediate stages | ||
| * All [approval nodes](../creating-application/workflow/cd-pipeline.md#manual-approval-for-deployment) of the intermediate stages | ||
|
|
||
|  | ||
|
|
||
|
|
||
| --- | ||
|
|
||
| ## Creating an Image Promotion Policy | ||
|
|
||
| {% hint style="warning" %} | ||
| ### Who Can Perform This Action? | ||
| Users need to have super-admin permission to create an image promotion policy. | ||
| {% endhint %} | ||
|
|
||
| You can create a policy using our APIs or through [Devtron CLI](https://github.com/devtron-labs/devtron-cli). Here is the CLI approach: | ||
|
|
||
| **Syntax**: | ||
| ``` | ||
| devtron-cli create imagePromotionPolicy \ | ||
ashokdevtron marked this conversation as resolved.
Show resolved
Hide resolved
|
||
| --name="policyName" \ | ||
| --description="desc" \ | ||
| --passCondition="true" \ | ||
| --failCondition="false" \ | ||
| --approverCount=0 \ | ||
| --allowRequestFromApprove=false \ | ||
| --allowImageBuilderFromApprove=false \ | ||
| --allowApproverFromDeploy=false \ | ||
| --applyPath="path/to/applyPolicy.yaml" | ||
| ``` | ||
|
|
||
| **Arguments**: | ||
|
|
||
| * `--name` (required): The name of the image promotion policy. | ||
| * `--description` (required): A brief description of the policy, preferably explaining what it does. | ||
ashokdevtron marked this conversation as resolved.
Show resolved
Hide resolved
|
||
| * `--passCondition` (optional): Specify a condition using [Common Expression Language (CEL)](https://github.com/google/cel-spec/blob/master/doc/langdef.md). Images that match this condition will be eligible for promotion to the target environment. | ||
| * `--failCondition` (optional): Images that match this condition will NOT be eligible for promotion to the target environment. | ||
| * `--approverCount` (optional): The number of approvals required to promote an image (0-6). Defaults to 0 (no approvals). | ||
| * `--allowRequestFromApprove` (optional): (Boolean) If true, user who raised the image promotion request can approve it. Defaults to false. | ||
| * `--allowImageBuilderFromApprove` (optional): (Boolean) If true, user who triggered the build can approve the image promotion request. Defaults to false. | ||
| * `--allowApproverFromDeploy` (optional): (Boolean) If true, user who approved the image promotion request can deploy that image. Defaults to false. | ||
| * `--applyPath` (optional): Specify the path to the YAML file that contains the list of applications and environments to which the policy should be applicable. | ||
|
|
||
| {% hint style="info" %} | ||
| If an image matches both pass and fail conditions, the priority of the fail condition will be higher. Therefore, such image will NOT be eligible for promotion to the target environment. | ||
| {% endhint %} | ||
|
|
||
| {% hint style="info" %} | ||
| If you don't define both pass and fail conditions, all images will be eligible for promotion. | ||
| {% endhint %} | ||
|
|
||
| --- | ||
|
|
||
|
|
||
| <!-- {% hint style="warning" %} | ||
| ### Who Can Perform This Action? | ||
| Users need to have super-admin permission to create an image promotion policy. | ||
| {% endhint %} | ||
|
|
||
| 1. Go to **Global Configurations** → **Image Promotion Policy**. | ||
abhibhaw marked this conversation as resolved.
Show resolved
Hide resolved
|
||
|
|
||
| 2. Click **Create Policy** on the top-right. | ||
|
|
||
| 3. Give a name to the policy and write a brief description, preferably explaining what it does. | ||
|
|
||
| 4. Under **Image Filter Condition**, you can enter the conditions which your image promotion should be subjected to (e.g., *`branchName.startsWith('hotfix')`*) | ||
|
|
||
| {% hint style="info" %} | ||
| Use **View filter criteria** to check the supported variables. | ||
| {% endhint %} | ||
|
|
||
| 5. You can specify either a pass condition, fail condition, or both conditions using [Common Expression Language (CEL)](https://github.com/google/cel-spec/blob/master/doc/langdef.md): | ||
| * **Pass Condition**: Images that match this condition will be eligible for promotion to the target environment. | ||
| * **Fail Condition**: Images that match this condition will NOT be eligible for promotion to the target environment. | ||
|
|
||
| {% hint style="info" %} | ||
| If an image matches both pass and fail conditions, the priority of the fail condition will be higher. Therefore, such image will NOT be eligible for promotion to the target environment. | ||
| {% endhint %} | ||
|
|
||
| {% hint style="info" %} | ||
| If you don't define both pass and fail conditions, all images will be eligible for promotion. | ||
| {% endhint %} | ||
|
|
||
| 6. (Optional) If required, you can setup approval requirements for this policy. If **Approval for Image Promotion Policy** is enabled, an [approval will be required for an image]((#approving-image-promotion-request)) to be directly promoted to the target environment. Only the users having 'Artifact promoter' role (for the application and environment) will be able to approve the image promotion request. | ||
|
|
||
| * **Number of Approvals (1-6)**: Specify the number of approvals required to promote an image. This can vary from one approval (minimum) to six approvals (maximum). | ||
|
|
||
| * **Checkboxes for who can approve**: As a super-admin, you also have options to control the approval of image promotion and its deployment. These are available in the form of checkboxes. | ||
|
|
||
| 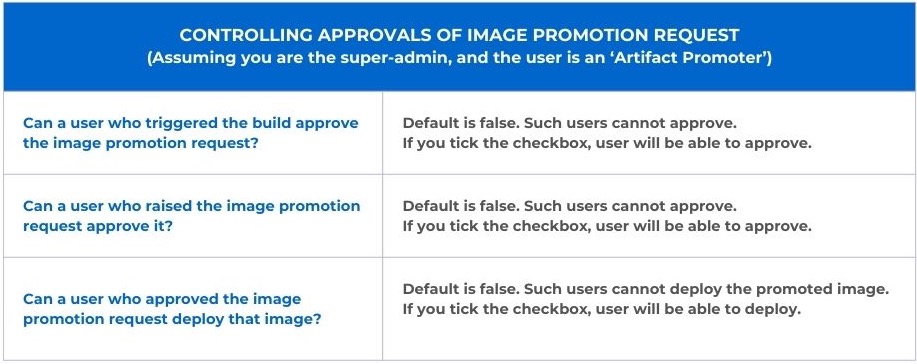 | ||
|
|
||
| 6. Click **Save Changes**. | ||
|
|
||
| --- | ||
|
|
||
| ## Applying an Image Promotion Policy | ||
|
|
||
| {% hint style="warning" %} | ||
| ### Who Can Perform This Action? | ||
| Users need to have super-admin permission to apply an image promotion policy. | ||
| {% endhint %} | ||
|
|
||
| Here, you can decide the application(s) and environment(s) for which image promotion is allowed. | ||
|
|
||
| 1. Go to the **Apply Policy** tab. | ||
|
|
||
| 2. Click the `Promotion Policy` dropdown next to the application, and choose the policy you wish to apply. | ||
|
|
||
| 3. A confirmation dialog box would appear. Click **Confirm**. | ||
|
|
||
| ### Performing Bulk Action | ||
|
|
||
| 1. You can also apply a policy to multiple applications and environments ('App+Env' combinations) in bulk. | ||
|
|
||
| 2. Simply use the checkboxes to select the desired application + environment combinations. | ||
|
|
||
| 3. You will see a draggable floating widget. Click **Change Policy** in the widget and select a desired policy to be applied to all your selections. | ||
|
|
||
| Moreover, there are three filters available to make the selections easier for you: | ||
| * Application | ||
| * Environment | ||
| * Policy | ||
|
|
||
| --- --> | ||
|
|
||
| ## Applying an Image Promotion Policy | ||
|
|
||
| {% hint style="warning" %} | ||
| ### Who Can Perform This Action? | ||
| Users need to have super-admin permission to apply an image promotion policy. | ||
| {% endhint %} | ||
|
|
||
| You can apply a policy using our APIs or through [Devtron CLI](https://github.com/devtron-labs/devtron-cli). Here is the CLI approach: | ||
|
|
||
| * Create a YAML file and give it a name (say `applyPolicy.yaml`). Within the file, define the applications and environments to which the image promotion policy should apply, as shown below. | ||
|
|
||
| {% code title="applyPolicy.yaml" overflow="wrap" lineNumbers="true" %} | ||
| ```yaml | ||
| apiVersion: v1 | ||
| kind: artifactPromotionPolicy | ||
| spec: | ||
| payload: | ||
| applicationEnvironments: | ||
| - appName: "app1" | ||
| envName: "env-demo" | ||
| - appName: "app1" | ||
| envName: "env-staging" | ||
| - appName: "app2" | ||
| envName: "env-demo" | ||
| applyToPolicyName: "example-policy" | ||
| ``` | ||
| {% endcode %} | ||
|
|
||
| Here, `applicationEnvironments` is a dictionary that contains the application names (app1, app2) and the corresponding environment names (env-demo/env-staging) where the policy will apply. In the `applyToPolicyName` key, enter the value of the `name` argument you used earlier while [creating the policy](#creating-an-image-promotion-policy). | ||
|
|
||
| * Apply the policy using the following CLI command: | ||
|
|
||
| ``` | ||
| devtron-cli apply policy -p="path/to/applyPolicy.yaml" | ||
| ``` | ||
|
|
||
|
|
||
| ## Result | ||
|
|
||
| ### Promoting Image to Target Environment | ||
|
|
||
| {% hint style="warning" %} | ||
| ### Who Can Perform This Action? | ||
| Users with build & deploy permission or above (for the application and target environment) can promote an image if the image promotion policy is enabled. | ||
| {% endhint %} | ||
|
|
||
| Here, you can promote images to the target environment(s). | ||
|
|
||
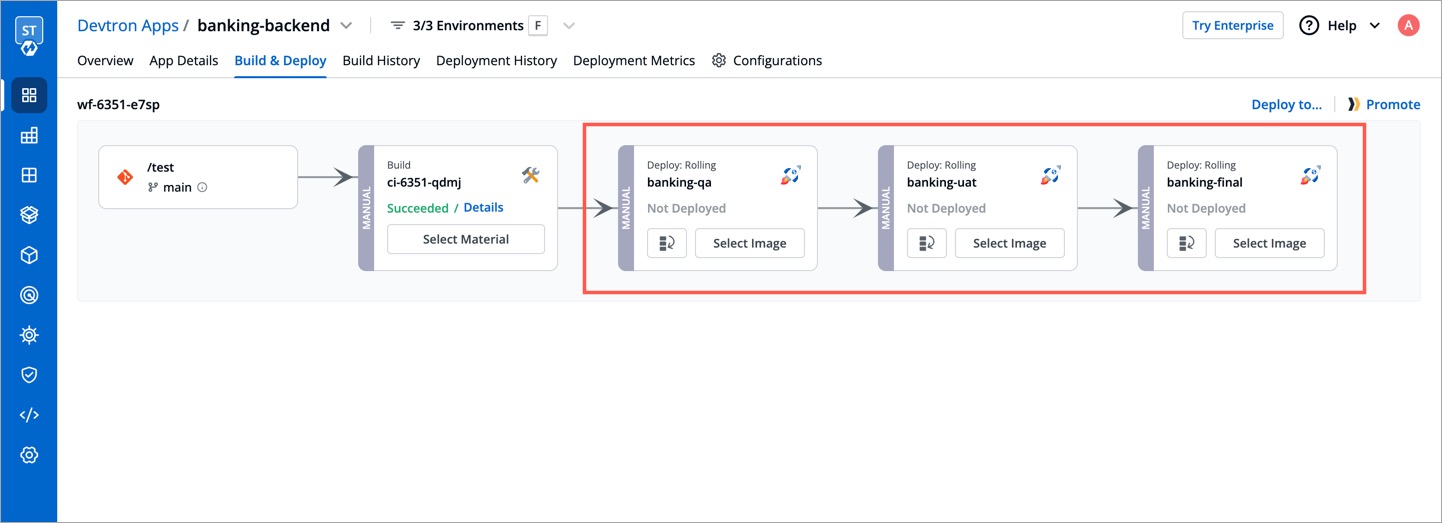
| 1. Go to the **Build & Deploy** tab of your application. | ||
|
|
||
| 2. Click the **Promote** button next to the workflow in which the you wish to promote the image. Please note, the button will appear only if image promotion is allowed for any environment used in that workflow. | ||
|
|
||
| 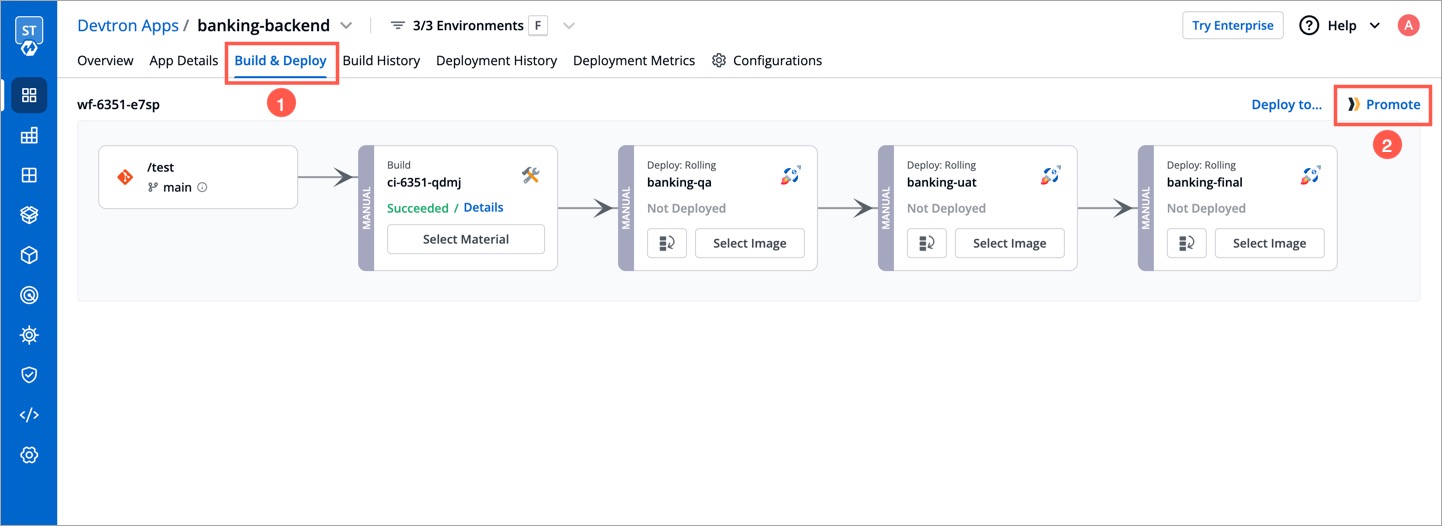 | ||
|
|
||
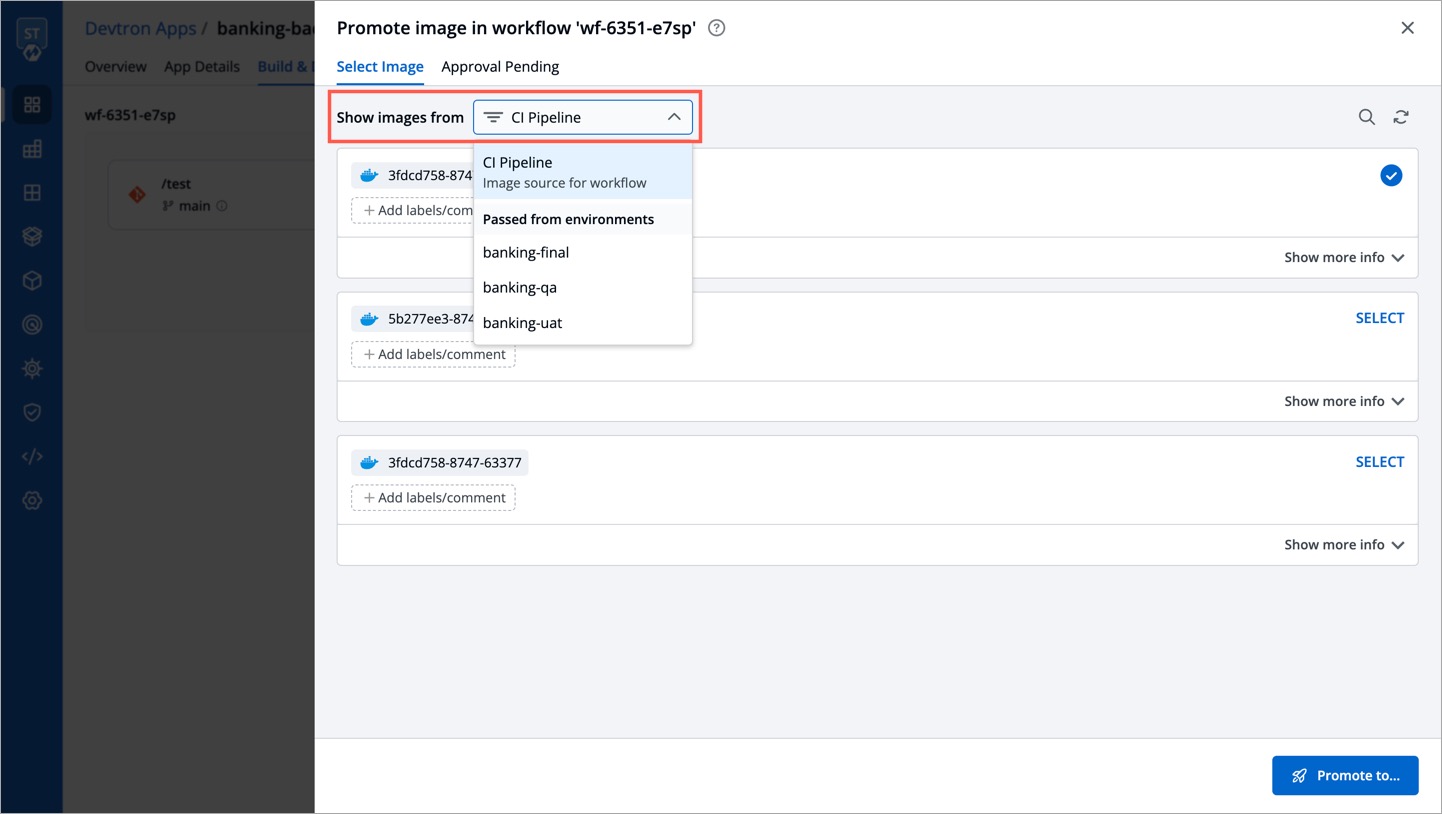
| 3. In the `Select Image` tab, you will see a list of images. Use the **Show Images from** dropdown to filter the list and choose the image you wish to promote. This can be either be an image from the CI pipeline or one that has successfully passed all stages (e.g., pre, post, if any) of that particular environment. | ||
|
|
||
|  | ||
|
|
||
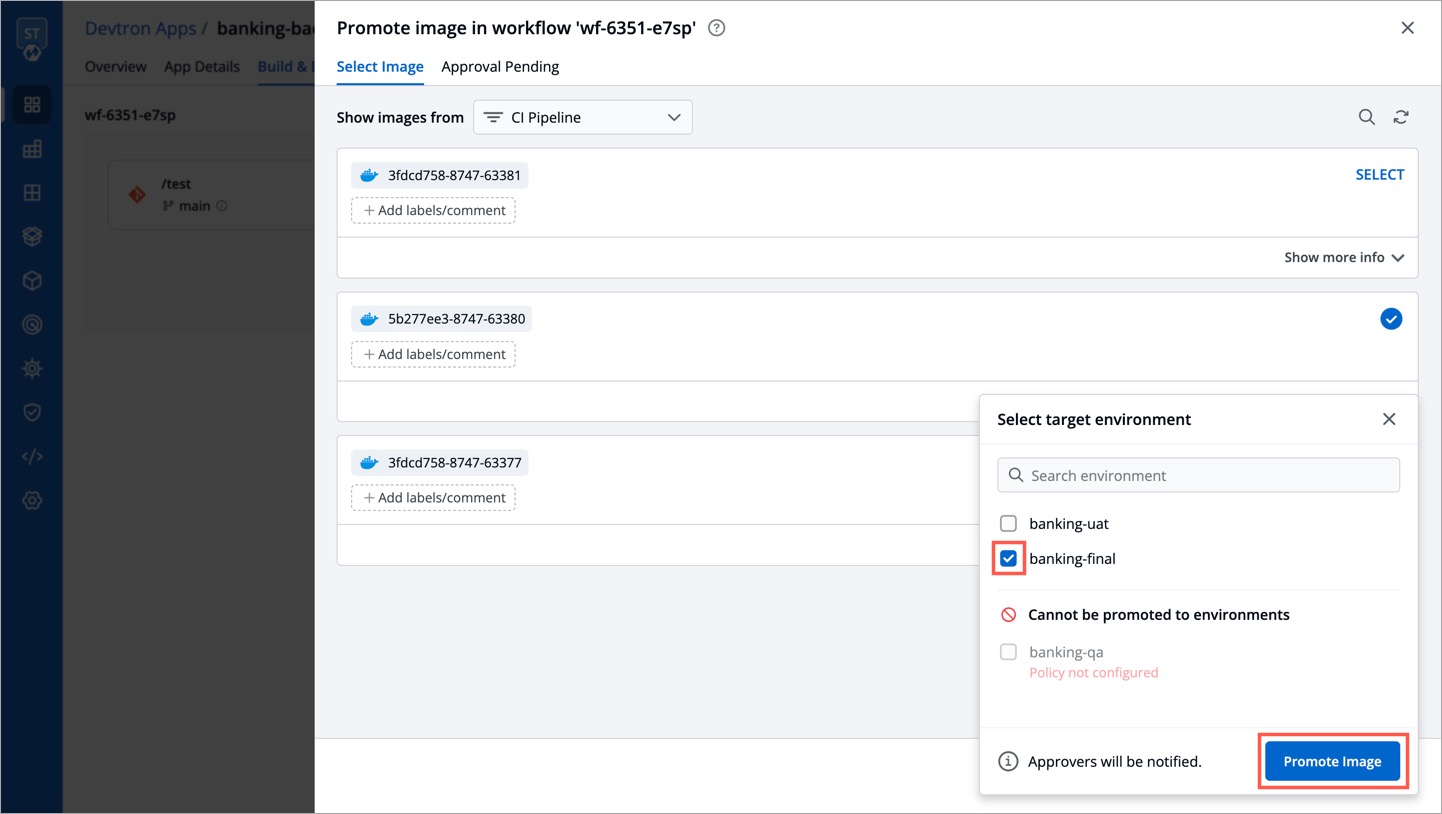
| 4. Use the **SELECT** button on the image, and click **Promote to...** | ||
|
|
||
| 5. Select one or more target environments using the checkbox. | ||
|
|
||
|  | ||
|
|
||
| 6. Click **Promote Image**. | ||
|
|
||
| The image's promotion to the target environment now depends on the approval settings in the image promotion policy. If the super-admin has enforced an approval process, the image requires the necessary number of approvals before promotion. On the other hand, if the super-admin has not enforced approval, the image will be automatically promoted since there is no request phase involved. | ||
|
|
||
| {% hint style="warning" %} | ||
| In case you have configured [SES or SMTP on Devtron](../global-configurations/manage-notification.md#notification-configurations), an email notification will be sent to the approvers. | ||
| {% endhint %} | ||
|
|
||
| 7. If approval(s) are required for image promotion, you may check the status of your request in the `Approval Pending` tab. | ||
|
|
||
| ### Approving Image Promotion Request | ||
|
|
||
| {% hint style="warning" %} | ||
| ### Who Can Perform This Action? | ||
| Only the users having [Artifact promoter](./user-access.md#role-based-access-levels) role (for the application and environment) or superadmin permissions will be able to approve the image promotion request. | ||
| {% endhint %} | ||
|
|
||
| 1. Go to the **Build & Deploy** tab of your application. | ||
|
|
||
| 2. Click the **Promote** button next to the workflow. | ||
|
|
||
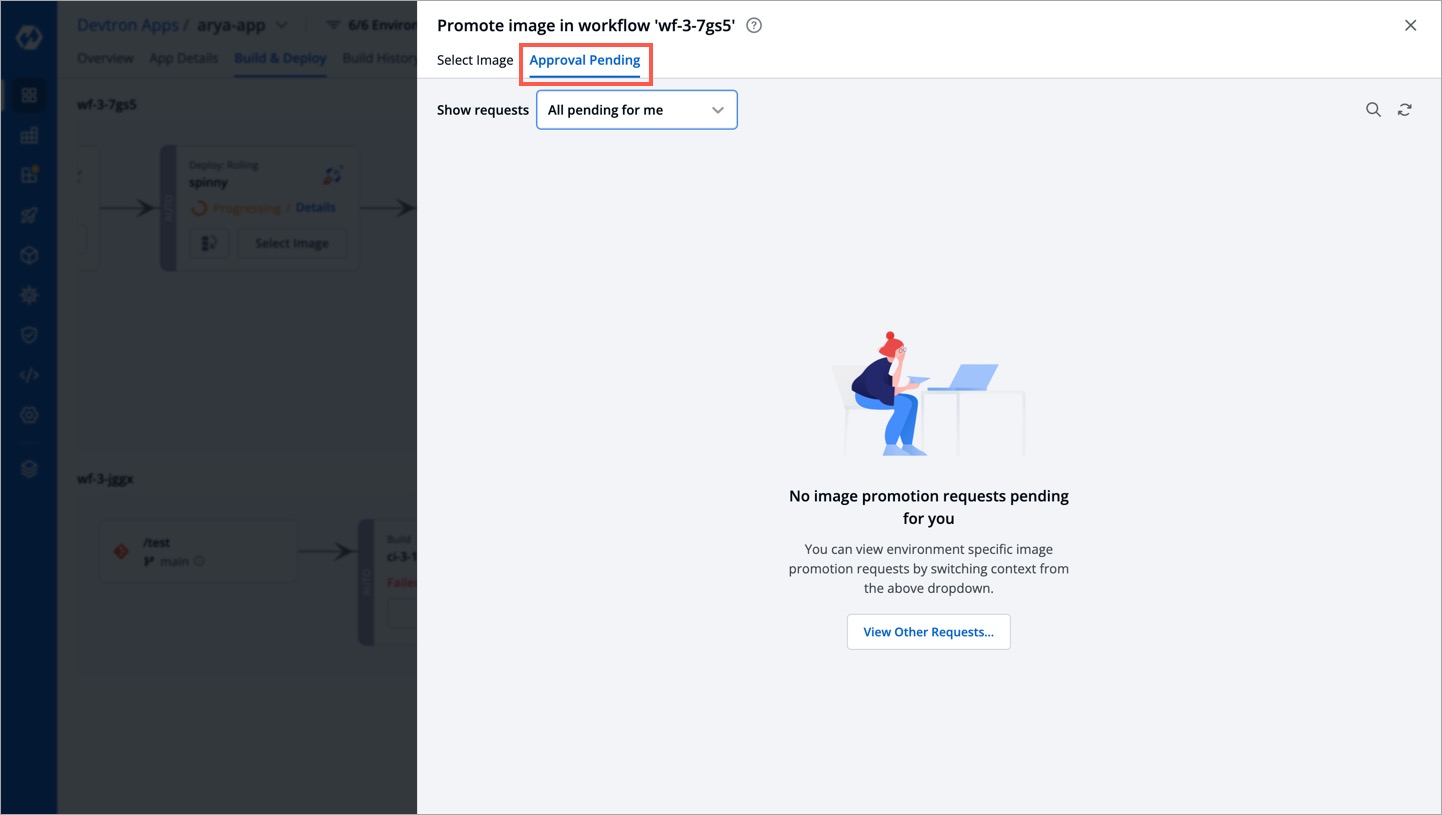
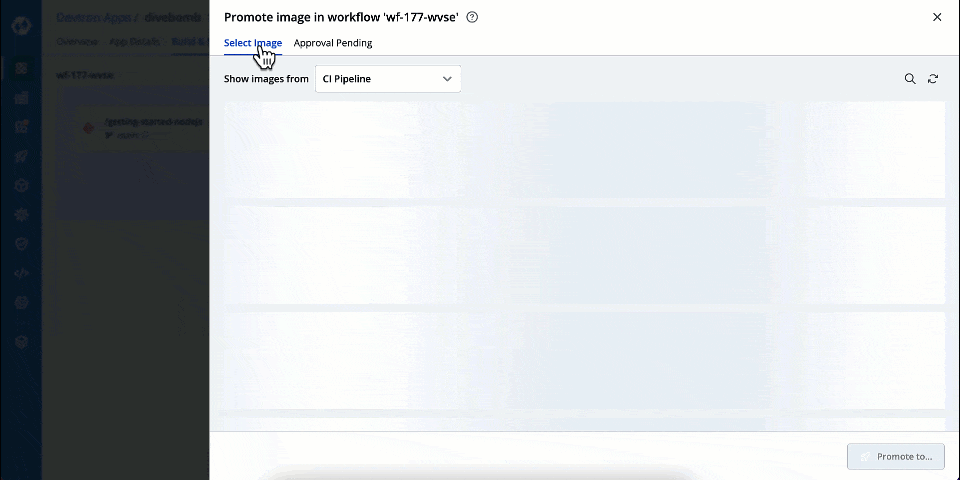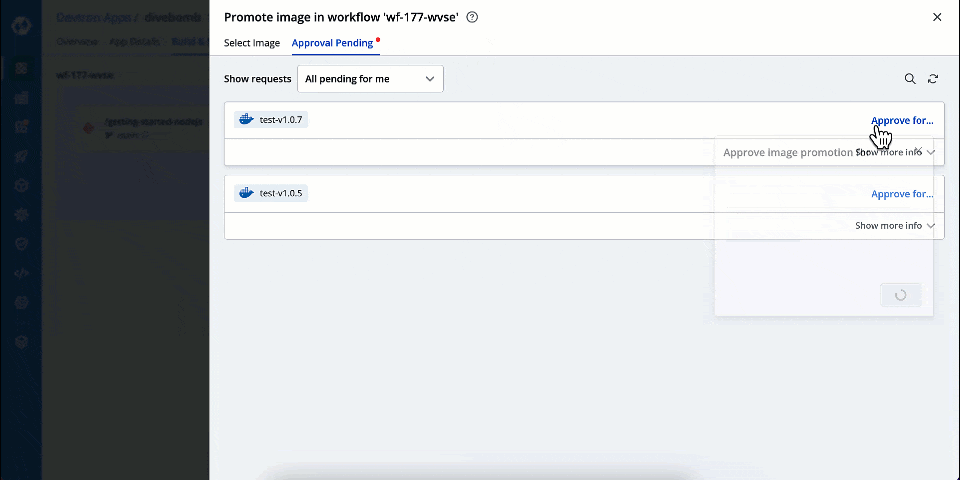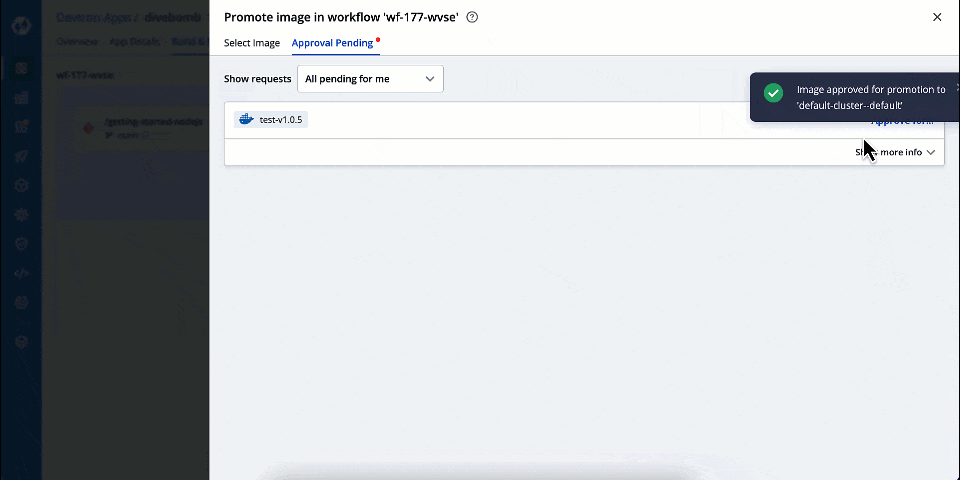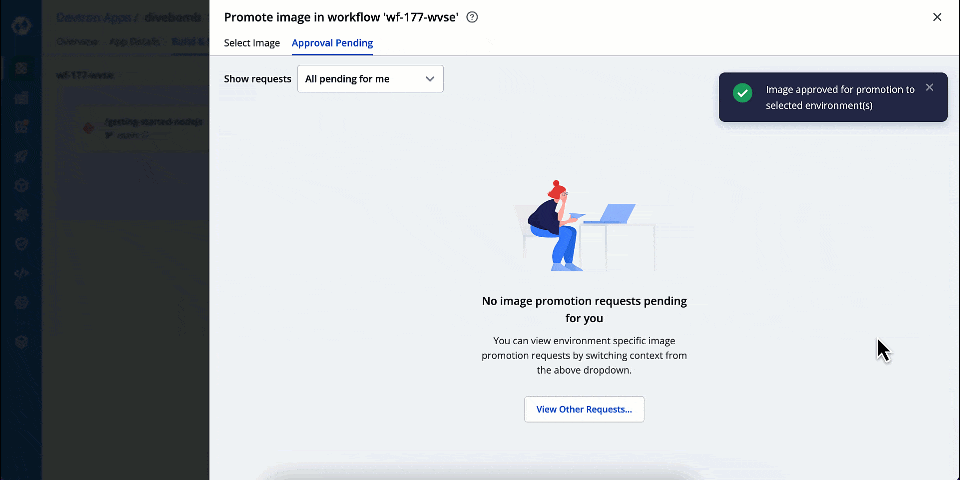
| 3. Go to the `Approval Pending` tab to see the list of images requiring approval. By default, it shows a list of all images whose promotion request is pending with you. | ||
|
|
||
|  | ||
|
|
||
| {% hint style="info" %} | ||
| All the images will show the source from which it is being promoted, i.e., CI stage or intermediate stage (environment). | ||
| {% endhint %} | ||
|
|
||
| 4. Click **Approve for...** to choose the target environments to which it can be promoted. | ||
|
|
||
| 5. Click **Approve**. | ||
|
|
||
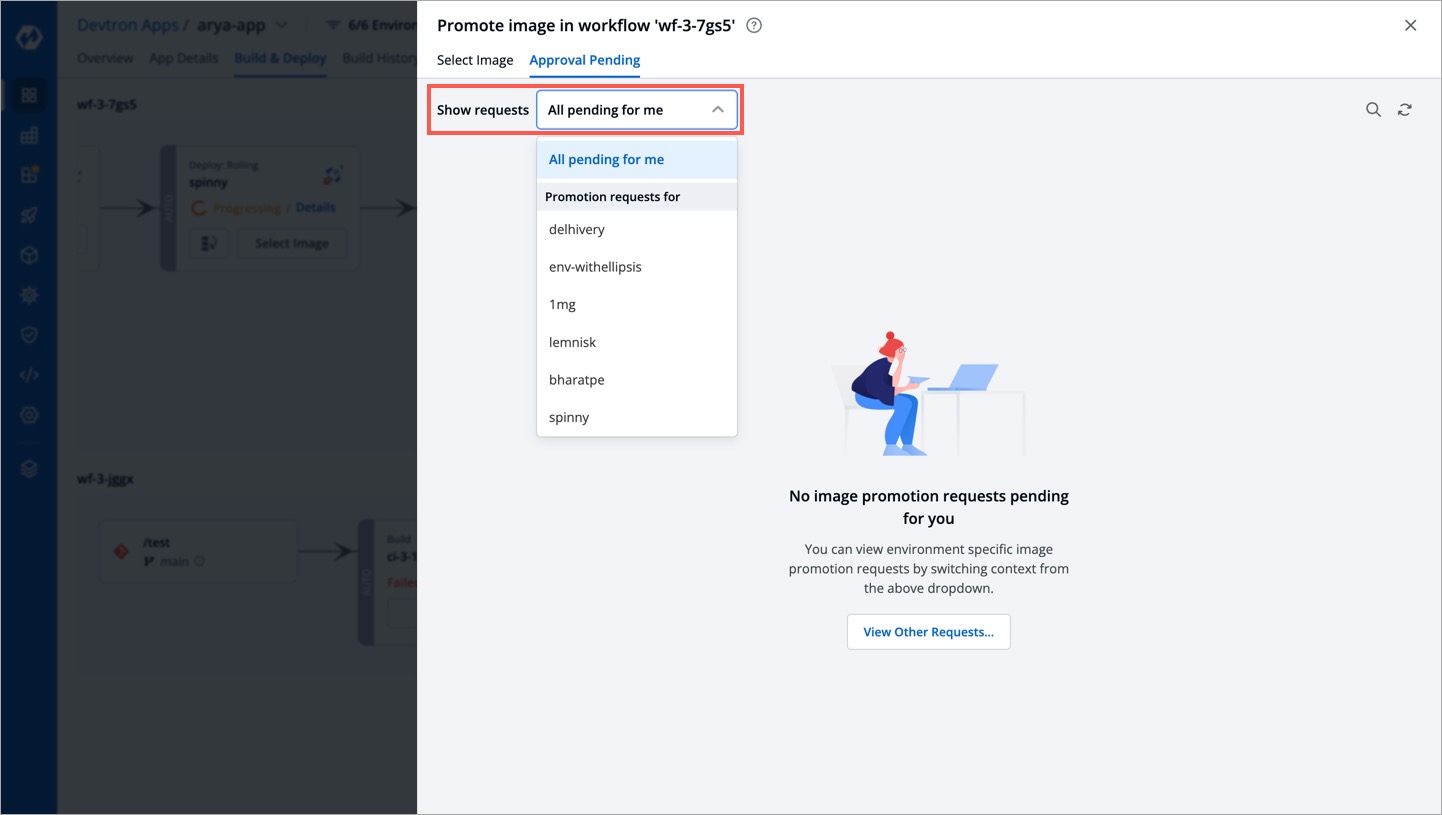
| You can also use the **Show requests** dropdown to filter the image promotion requests for a specific target environment. | ||
|
|
||
|  | ||
|
|
||
| If there are pending promotion requests, you can approve them as shown below: | ||
|
|
||
|  | ||
|
|
||
| ### Deploying a Promoted Image | ||
|
|
||
| {% hint style="warning" %} | ||
| ### Who Can Perform This Action? | ||
| Users with build & deploy permission or above for the application and environment can deploy the promoted image. | ||
| {% endhint %} | ||
|
|
||
| If a user has approved the promotion request for an image, they may or may not be able to deploy depending upon the [policy configuration](#creating-an-image-promotion-policy). | ||
|
|
||
| However, a promoted image does not automatically qualify as a deployable image. It must fulfill all configured requirements ([Image Deployment Approval](../creating-application/workflow/cd-pipeline.md#manual-approval-for-deployment), [Filter Conditions](./filter-condition.md), etc.) of the target environment for it to be deployed. | ||
|
|
||
| In the **Build & Deploy** tab of your application, click **Select Image** for the CD pipeline, and choose your promoted image for deployment. | ||
|
|
||
| 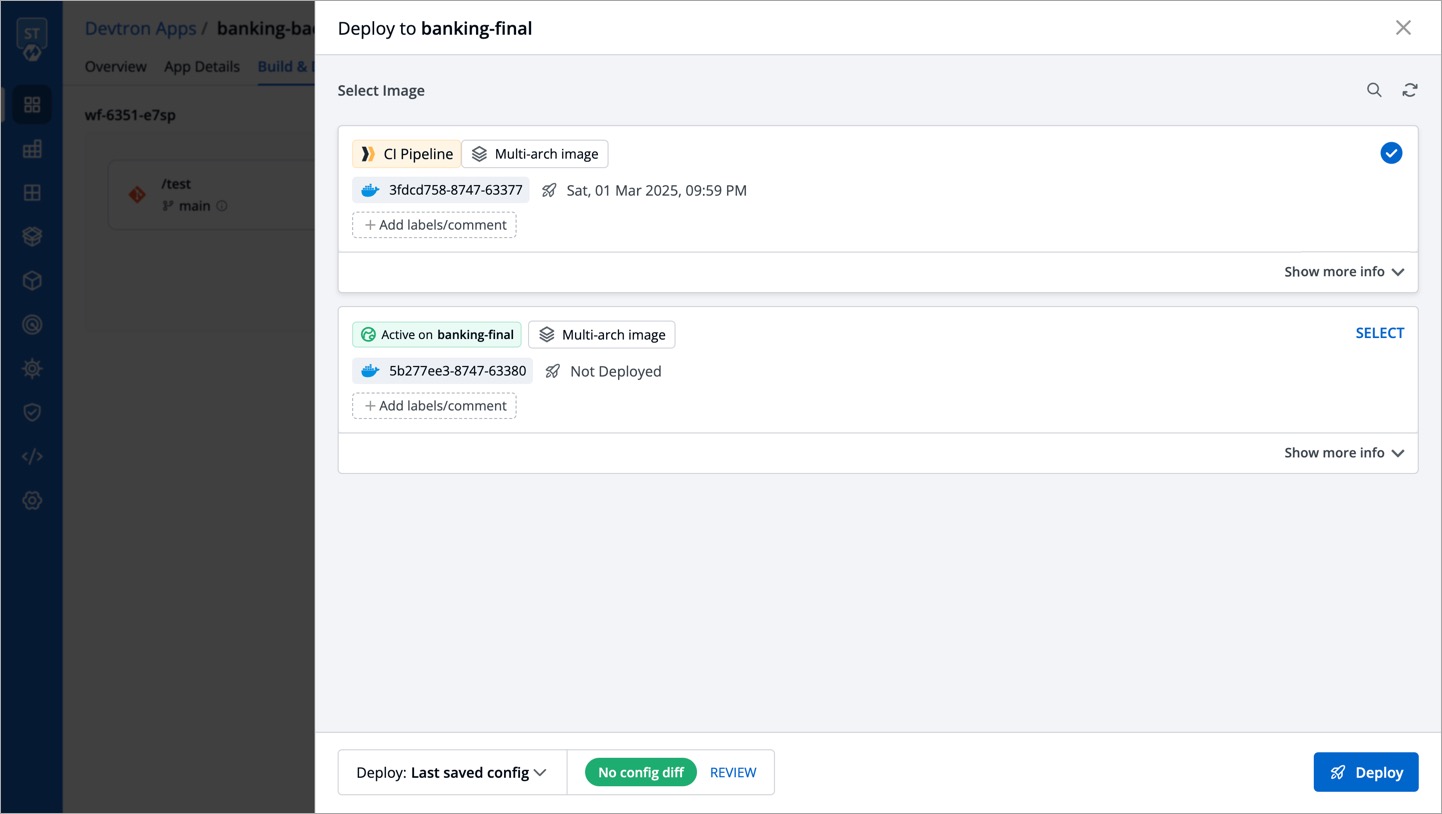 | ||
|
|
||
| You can check the deployment of promoted images in the **Deployment History** of your application. It will also indicate the pipeline from which the image was promoted and deployed to the target environment. | ||
|
|
||
| 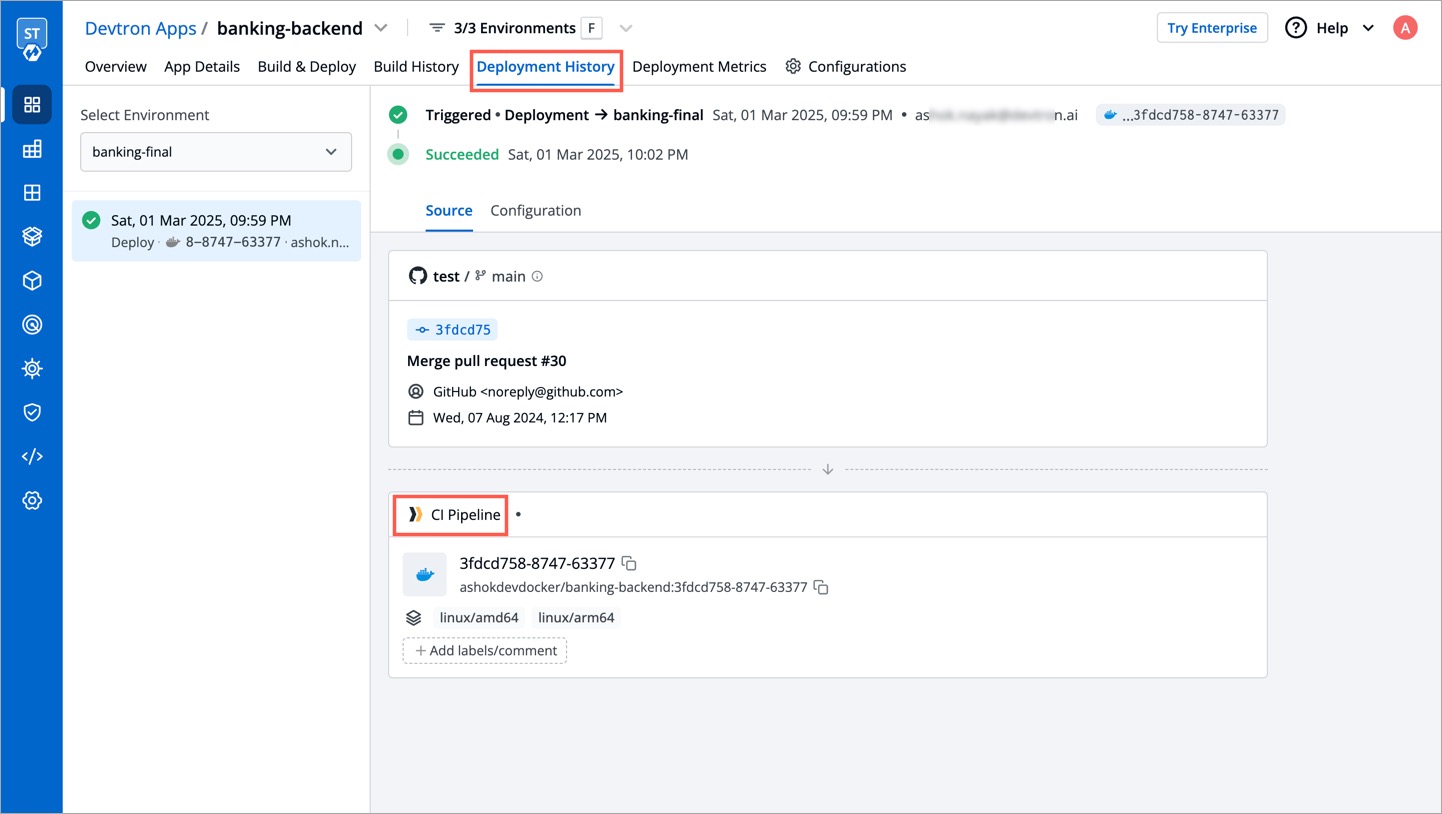 | ||
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
Add this suggestion to a batch that can be applied as a single commit.
This suggestion is invalid because no changes were made to the code.
Suggestions cannot be applied while the pull request is closed.
Suggestions cannot be applied while viewing a subset of changes.
Only one suggestion per line can be applied in a batch.
Add this suggestion to a batch that can be applied as a single commit.
Applying suggestions on deleted lines is not supported.
You must change the existing code in this line in order to create a valid suggestion.
Outdated suggestions cannot be applied.
This suggestion has been applied or marked resolved.
Suggestions cannot be applied from pending reviews.
Suggestions cannot be applied on multi-line comments.
Suggestions cannot be applied while the pull request is queued to merge.
Suggestion cannot be applied right now. Please check back later.
Uh oh!
There was an error while loading. Please reload this page.